kreuzwerker MSP onboarding covers all steps necessary to get you up and running quick and easy. This usually includes:
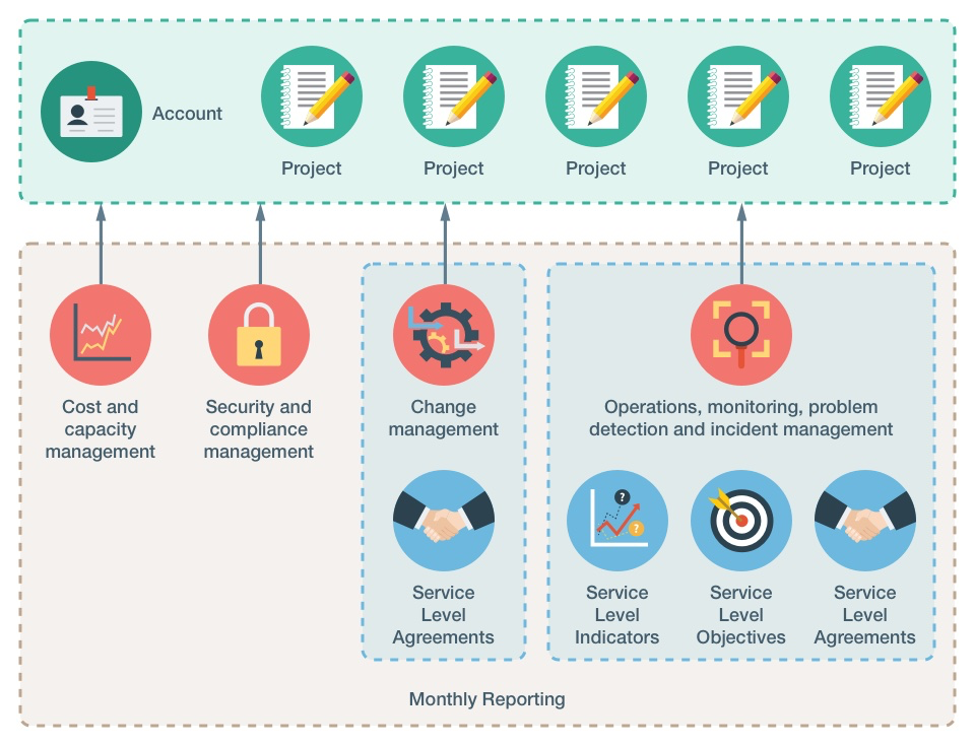
- Account creation using a flat (single) account or star (e.g. customer root and customer live / test) account structure or management of existing accounts and subsequent configuration according to best-practices
- Cost and Capacity Management yielding e.g. the proposal of buying into reserved instances schemas
- Continuous Security and Compliance monitoring process
- Change, Incident and Problem Management triggered by automated supervision of service-level objectives and customer requests through a service desk
- Extensive Metrics collection and aggregation in Dashboards
- Optional Monthly Reporting over the results of the continuous compliance and cost processes, including the service level agreement and objectives hits and misses
- Provisioning of kreuzwerker specific Infrastructure and Tooling for additional features and secure interactions with the AWS APIs
Depending on your level of expertise this program will enable your organization to get their deployment interfaces up and running, manage cost, security and compliance aspects of your account(s) better or begin managing them for the first time. If you are already an enterprise or power-user of AWS this program can result in a bootstrapping process for Cloud Competence Centers that enables your organization to follow the best practice patterns of a next-generation managed service provider and apply the optimizations we previously delivered to you to your internal customers.
In the shared responsibility model AWS remains responsible for the security of the Cloud. kreuzwerker as the next-generation managed service provider helps your organizations maintain their part in the model: the security in the Cloud.
The following document describes your voyage into the MSP, describes the feature-set in detail as well as the off-boarding process when leaving the MSP program.
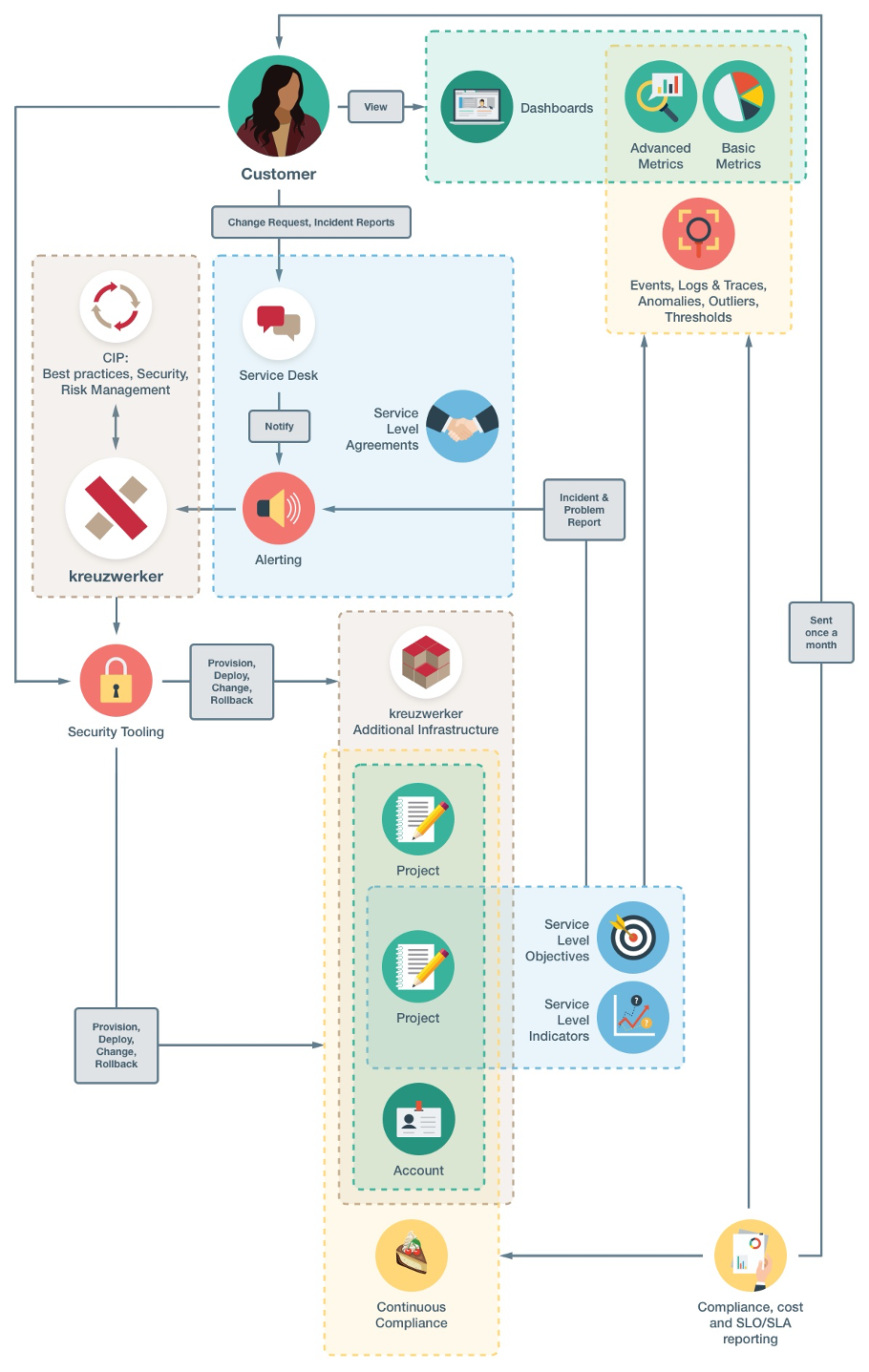
Change and Incident management: service desk, monitoring and service levels
Our support is available to you via a dedicated Service Desk either via web-portal or E-Mail. Dedicated SLAs add availability via Telephone.
Besides the service desk we offer individual monitoring models for pro-actively managing Service Level Agreements (SLA).
Monitoring can be implemented for different levels of your solution eg. compliance conformity, infrastructure availability, operating system parameters, Service Level Objective (SLO) with underlying Service Level Indicator (SLI) e.g. Apdex at customers discretion. Monitoring is further available in these foundational models.
Please consider our foundational service level agreement to consider the impact of the levels you can choose when requesting a change or reporting an incident within the above monitoring times.
Access control and user management
Our security concept involves the following core concepts:
- Avoid the usage of long-term credentials for machines and people
- Usage of multiple second factors (apart from the access keys) to protect against loss of hardware, phishing, compromised backups etc.
- Use least-privilege policies wherever applicable
Currently our custom tooling supports the following seconds factors:
- Fixed IP addresses where the operators must execute API calls from - this can be the external IP address of a developer network in your company
- YubiKey USB smartcard with OATH soft-tokens configured
- Account ID and (optionally) external ID for connections from other AWS accounts
We use both of those second factors as well as custom tooling for our access control.
With this concept in place you have two choices:
- Continue using regular IAM users with long-term credentials and maintain them on your own
- Use the IAM groups and roles we provision - this means we will provision IAM users for you through a CR
Operations
In order for kreuzwerker to operate on your infrastructure a number of prerequisites need to be met:
- Automation: all infrastructure provisioning must be done through automation, either with CloudFormation or Terraform and we have access to the templates or configuration sources
- Auto recovery or high availability option: infrastructure must recover automatically, semi-automatically (through infrastructure tooling) or be highly available
- Compliance: can be monitored and operated in a safe and sensible manner - this requires infrastructure either be designed or audited by kreuzwerker
- Encryption (at rest): infrastructure that supports encryption-at-rest must use it
- VPC: infrastructure that supports VPC must be deployed in a VPC
With these prerequisites met, we can perform the following operation types, driven through monitoring or explicit requests through the service desk:
- Incident management
- Change management
- Patch management
- Release and deployment management
- Rollbacks
Currently we only support immutable operations.
- Host-level operations only on machine-images: we support patch management, change management and rollback options through CI/CD for Amazon Machine Images (AMI)
- Container-level operations only on Docker images: we support patch management, change management and rollback options through CI/CD for the ECS Docker Registry
Reporting & Continual Service Improvement
For continual service review and improvement metrics, reports and regular review meetings can be defined and agreed as per customer discretion and availability. We recommend during Ramp-up a weekly call and monthly in-person meeting; in Operations a weekly virtual stand-up, every 2 months an in-person review and on-demand for substantial change requests or incidents.
Data privacy, ownership of data and responsibilities
Please find below excerpts from AWS EU Data Protection statement which we also apply to our contractual relationship.
There are 2 types of data to be differentiated - customer content and account information.
We define customer content as software (including machine images), data, text, audio, video or images that a customer or any end user transfers to us for processing, storage or hosting by AWS services in connection with that customer’s account and any computational results that a customer or any end user derives from the foregoing through their use of AWS services. The terms of the AWS Customer Agreement or other agreement with us governing the use of AWS services apply to your customer content.
We will never access customer content out of own initiative but only on your request with written order.
Customers maintain ownership of their customer content and select which AWS services process, store and host their customer content. We do not access or use customer content for any purpose without the customer’s consent. We never use customer content or derive information from it for marketing or advertising.
We define account information as information about a customer that a customer provides to us in connection with the creation or administration of a customer account. The information practices described in the AWS Privacy Notice apply to account information. See AWS EU-Data-Protection for more information.
Customer accounts, managed as member of kreuzwerker organization; see “setup and on-boarding”, are in ownership of the customer and thus all activities performed with provided IAM users of the account are in the responsibility of the customer. kreuzwerker will never use customer’s IAM users for any activities but cross-account roles.
For compliance with the GDPR, please a) see our privacy policy page and b) the set-up data processing contract with you.
Access to managed resources
As per the AWS Shared Responsibility Model- you, kreuzwerker and AWS share the responsibility within the cloud.
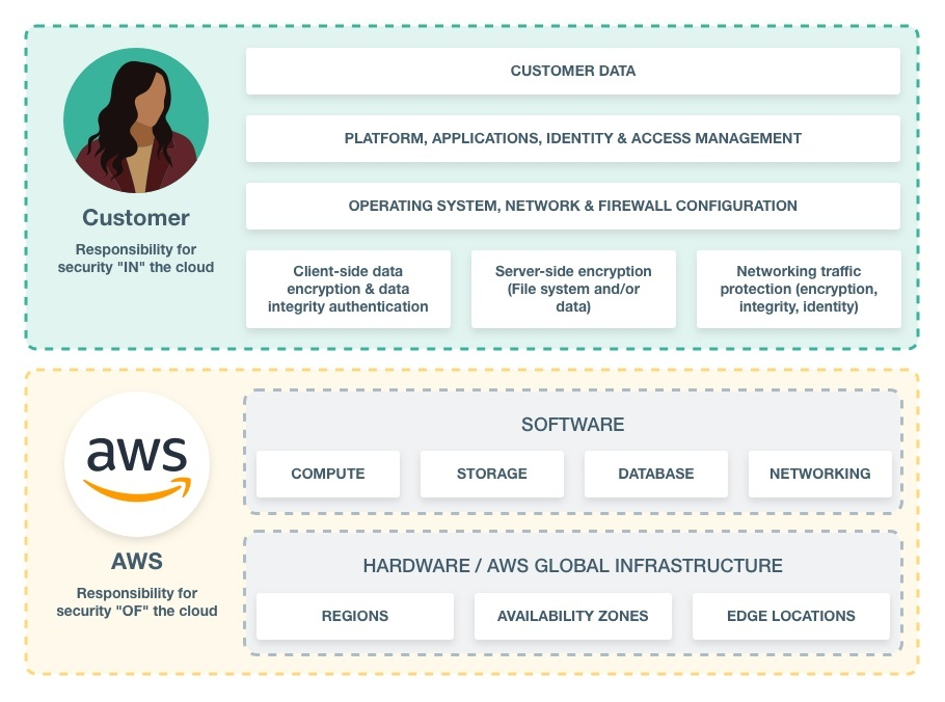
As kreuzwerker and you share the above displayed customer part, the split happens in the following way. From this split certain access restrictions apply:
- kreuzwerker have no access to the Operating System Level and above of your Compute Resources (eg. SSH access to EC2 instances, Cluster nodes etc.)
- kreuzwerker have no access to internal management of instantiated services (eg. permission system of Database Management System, ElastiCache etc.)
- kreuzwerker do provide backup and restore facilities of the compute stack and managed services.
Our partner

